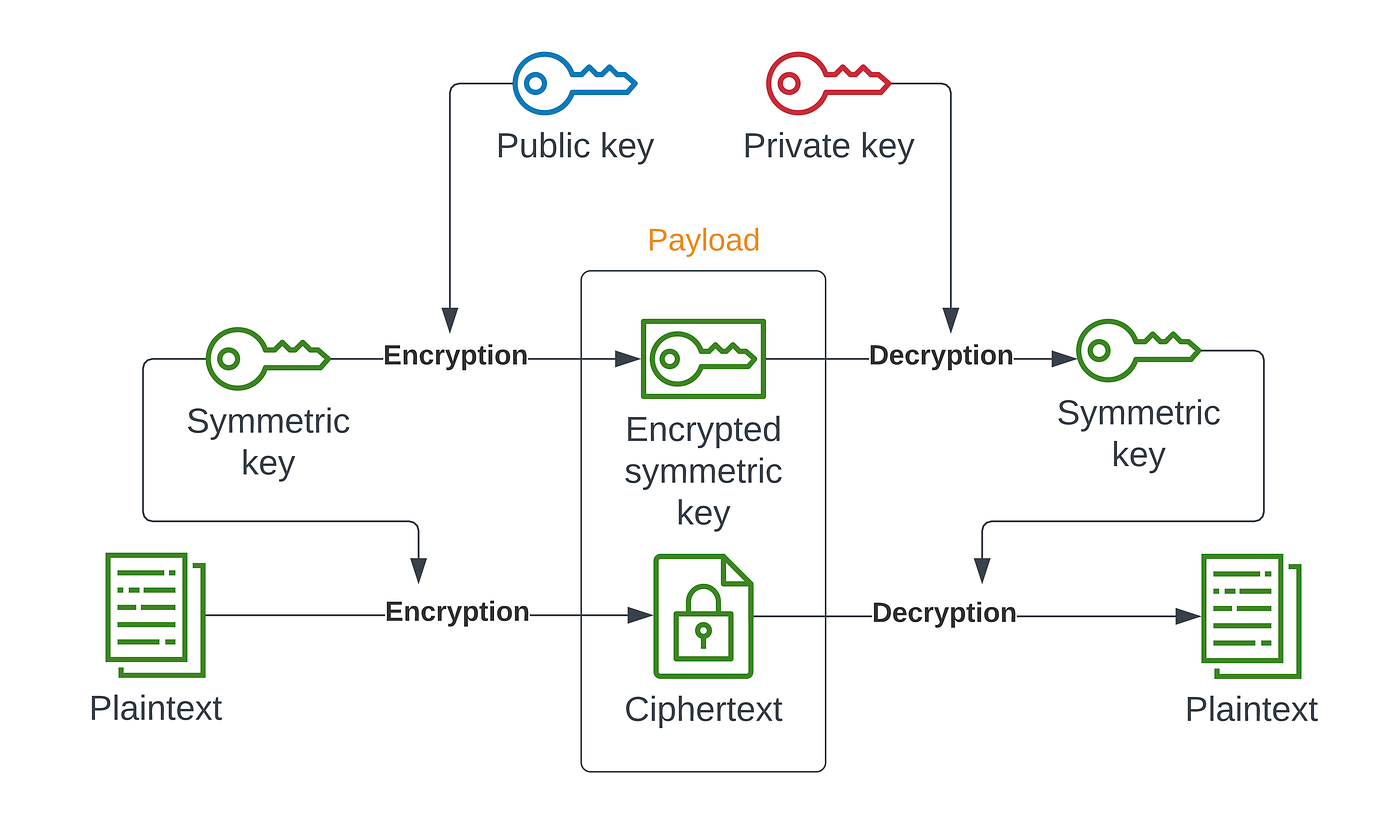
Figure 1 from Hybrid cryptography mechanism for securing self-organized wireless networks | Semantic Scholar
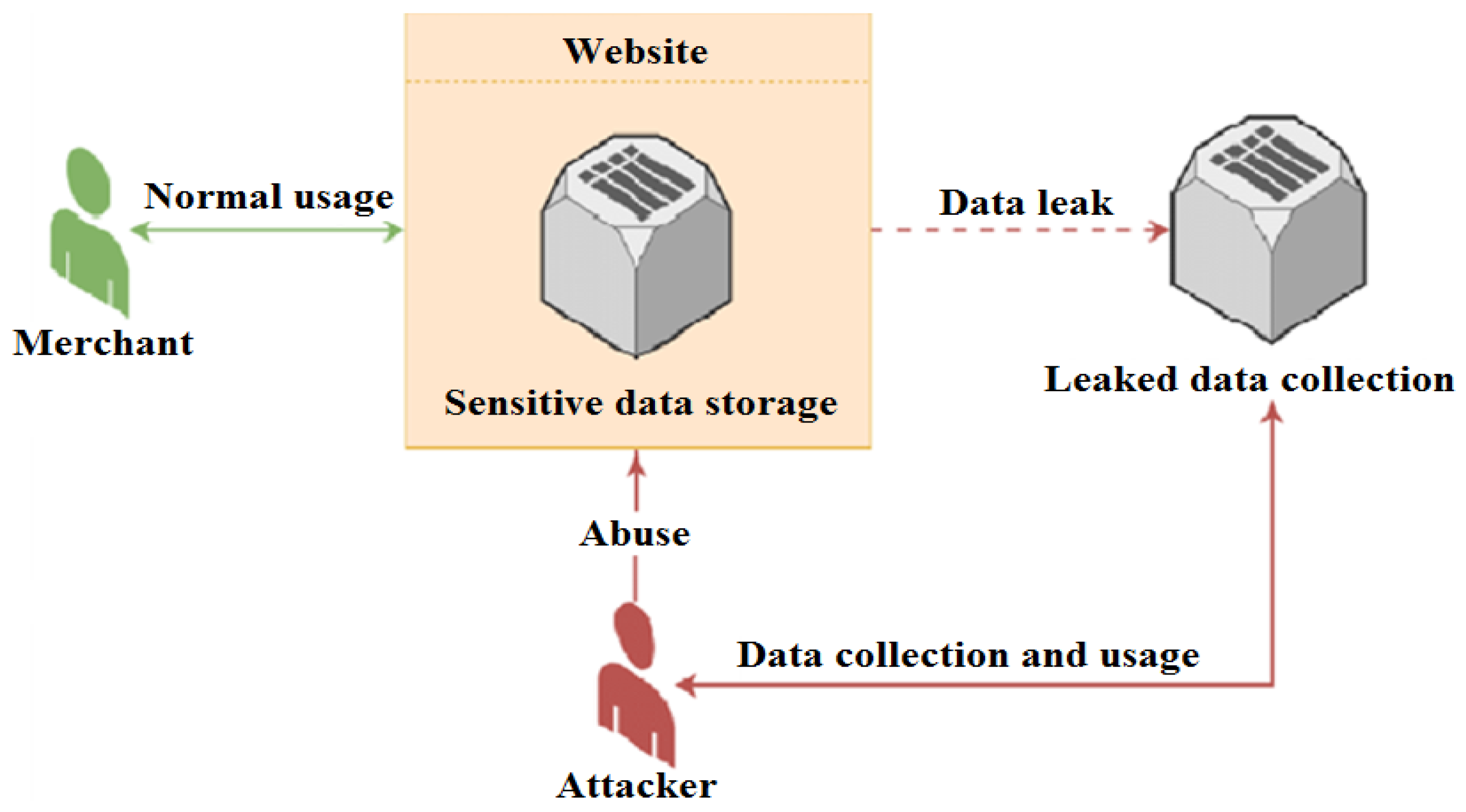
Future Internet | Free Full-Text | Applying Detection Leakage on Hybrid Cryptography to Secure Transaction Information in E-Commerce Apps

A Comparative Study of Various Traditional and Hybrid Cryptography Algorithm Models for Data Security | SpringerLink
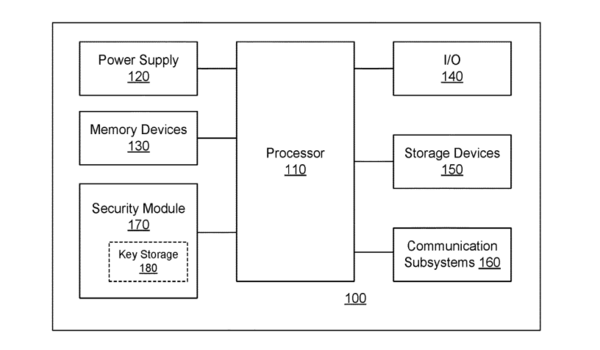
Quantum-augmentable hybrid encryption system and method - Ted Rogers School of Management - Toronto Metropolitan University
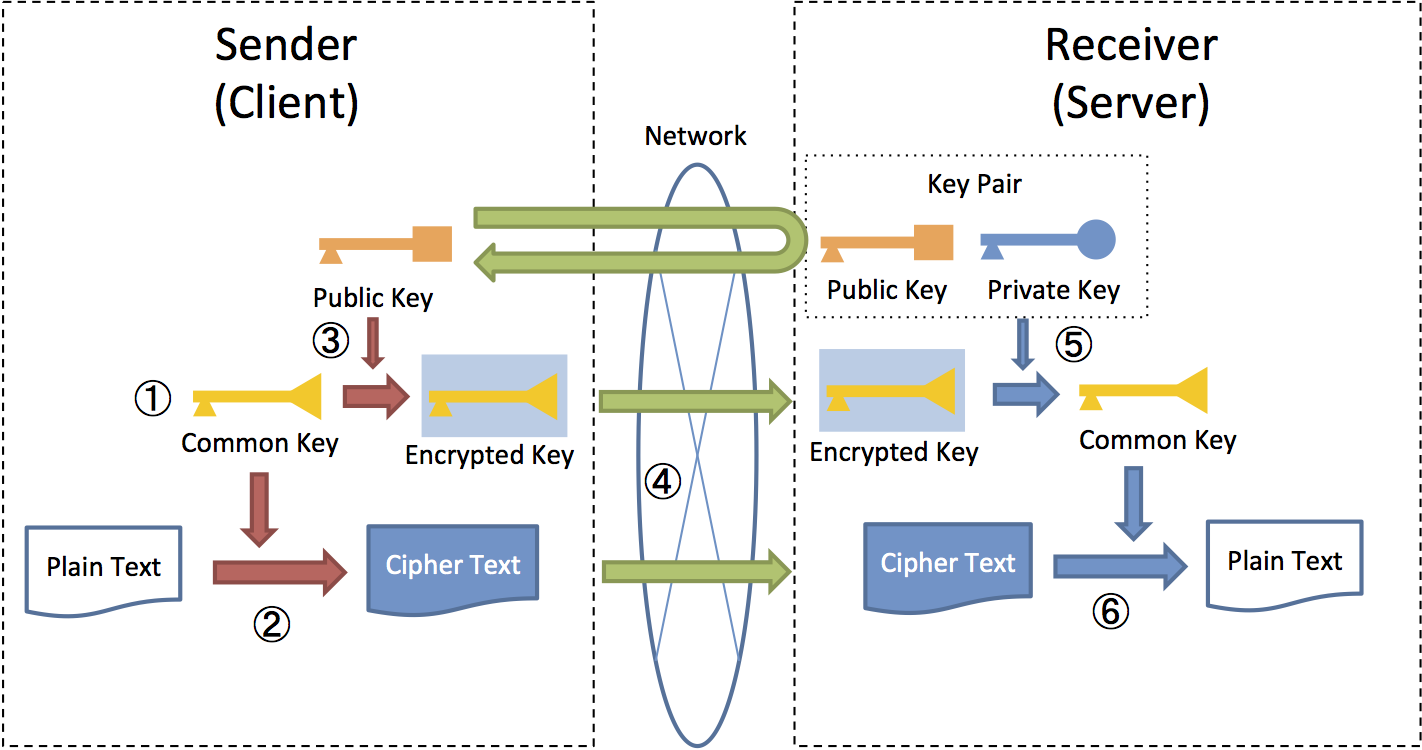
9.8. Encryption — TERASOLUNA Server Framework for Java (5.x) Development Guideline 5.4.1.RELEASE documentation

Hybrid encryption algorithm using Krishna and AES algorithms Figure 4,... | Download Scientific Diagram
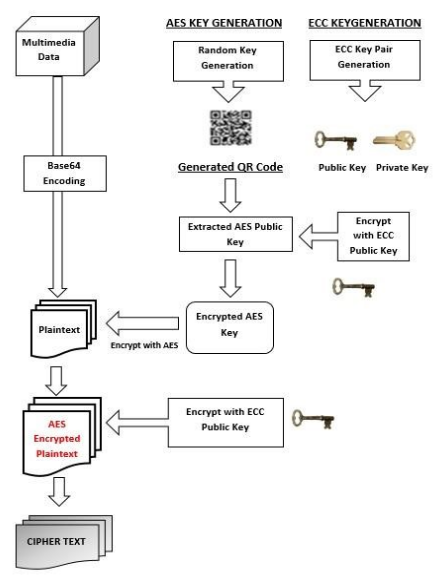
Hybrid-Cryptography | Implementation of a system capable of encryption and decryption of multimedia data (Text, Images, Videos, Audio etc.) using a hybrid model based on the amalgamation of symmetric encryption techniques such

A Hybrid Crypto System based on a new Circle- Symmetric key Algorithm and RSA with CRT Asymmetric key Algorithm for E-commerce Applications | Semantic Scholar